The continuous threat of cyber attacks on essential services, public safety and business systems remains at a high level as many organizations across the country have been impacted by incidents in the past few years. Foreign governments, like Russia, have used these cyber attacks as a key component in their objectives which has led to disabled or destroyed critical infrastructure.
Many of these cyber attacks have come with the assistance of tactics featuring misinformation, disinformation, and malinformation (MDM) to shape public opinion, undermine trust, amplify division, and sow discord. In connection with these objectives, suspicious links and phishing emails surrounding information classified as an MDM have been utilized to gain valuable information of individuals and organizations around the world.
The United States’ Cybersecurity and Infrastructure Security Agency (CISA) recently released detail on what steps can be taken by all persons to mitigate foreign influence that targets critical infrastructure and personal information. The action steps explained by CISA around developing a plan to combat these MDM tactics can be broken down into five stages: Assessment, Identification, Fortification, Engagement and Development.
Assessing the Information Environment
If there are specific MDM topics that are impacting your business sector, evaluating them and the impact they can have on your operations is the first step to understanding the potential threat. Next, learn how and where your stakeholders and customers receive information. By using these channels to understand what information they are taking in and how you can communicate with them, better allows you to respond to MDM activity and act as the trusted information source. Lastly, always be monitoring any changes to activity related to your sector or even your own organization. Be on the lookout for unusual changes such as a sudden increase in tags, followers, search inquiries, or other increases in contacts to your organization.
Identifying Vulnerabilities

Once any threats have been assessed, attention should then turn to what vulnerabilities could be exploited by these MDM tactics. CISA recommends thinking about common questions or points of confusion that people have about your sector or operations and then establish a criterion around evaluating the severity of such attacks.
Meanwhile internally, educate staff on securing any personal accounts including social media so they are aware what information is visible. Also, remind them to practice smart email hygiene and avoid clicking on or sharing any suspicious links that could make them or the organization vulnerable.
Hackers assist in surveillance or reconnaissance and provide opportunities for destructive attacks. Hijacking accounts and defacing public
facing sites can be used to influence public opinion. Organizations should be aware of cyber risks and take action to reduce the likelihood and impact of a potentially damaging compromise.
Fortify Communications Channels
Having a well thought out communication plan before MDM incidents occur can be the difference in how much you are impacted by such an event. Establish clear communication channels with stakeholders, employees, and customers to make verified sources clear and easily accessible. Ensure that these channels are well secured, have multi-factor authentication enabled and that unauthorized persons do not have access to post to those channels.
Engage in Proactive Communication
Engaging with clear, consistent, and relevant communications with the appropriate audiences is an effective way to maintain security, build public confidence and get ahead of any MDM threats that may exist. Encourage the use of professional networks and other organizations to amplify this messaging, resulting in a strong network of trusted voices within the sector. You will also want to use this time to look at ways to improve your communication including utilizing new platforms and opportunities to expand your reach.
Develop an Incident Response Plan
If your organization is impacted by any MDM tactics, it’s vital a plan is in place to respond to such situations. Establish a point person to oversee the process and any associated crisis communications. Other roles and responsibilities for ensuring a successful plan include responding to media inquiries, issuing public statements, internal communications, engaging stakeholders, implementing additional security measures.
While building this plan, consider what the current coordination processes are for identifying potential MDM incidents, controlling the information surrounding subject, and the channels utilized to position your organization as a trusted voice.
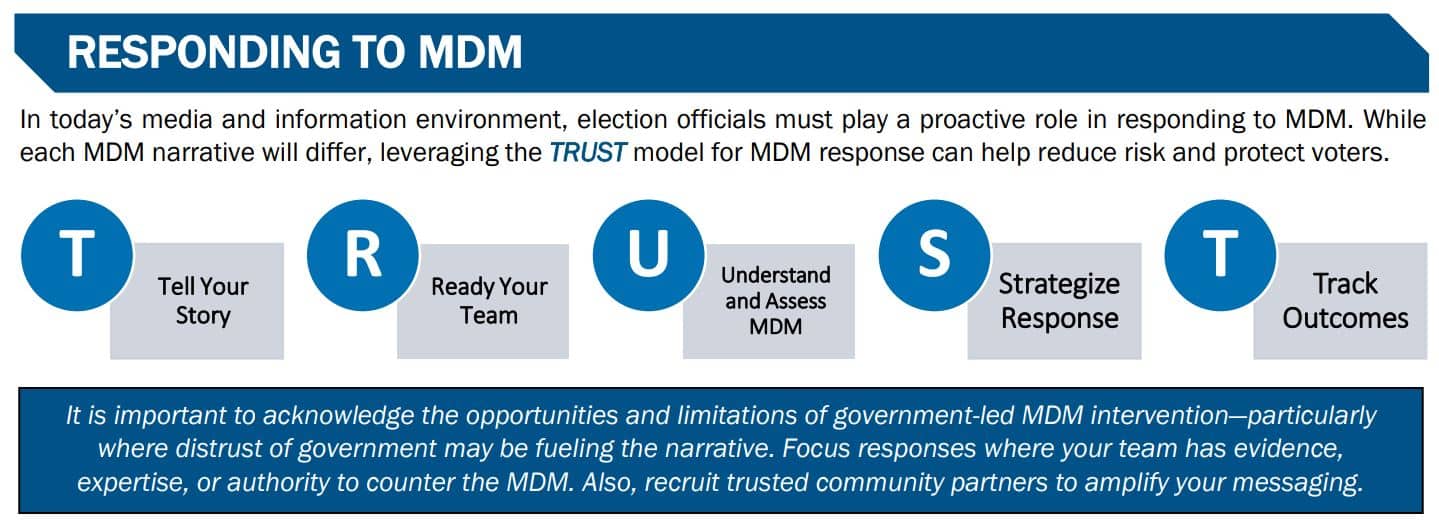
TRUST Method from the CISA
Shields Up Guidance for All Organizations from CISA
CISA recommends all organizations—regardless of size—adopt a heightened posture when it comes to cybersecurity and protecting their most critical assets. To learn more on preparing for foreign influence tactics, visit CISA’s report on all the steps that can be taken here: https://www.cisa.gov/sites/default/files/publications/cisa_insight_mitigating_foreign_influence_508.pdf
For more information on additional actions organizations and individuals can take to ensure they are not the victim of a cyber-attack, visit www.cisa.gov/shields-up.
About Titan Security Group
Titan launched in 1994 with a vision for a better way to provide security services to the Chicagoland community. Today, Titan is one of the largest security companies in North America, scheduling approximately 80,000 hours per week, employing more than 2,500 security staff, and have enjoyed over twenty-eight consecutive years of successfully serving our clients across a wide range of industries. Titan delivers results to clients through flexible, customized security solutions, and superior customer service. The Titan approach combines traditional security staffing with electronic security systems to provide integrated and efficient, customized security solutions from a single source.
